Configuring a LoRaWAN® AS routing profile for HSM
This task consists in activating a Hardware Security Module (HSM) on an AS routing profile you will associate with an OTAA device you want a hardware protection of the device's root keys. For more information, see Creating an OTAA device.
It generates the AS transport key used by the application server to decrypt the AppSKey, then the device payload. You will use an RSA key to generate the AS transport key.
Important ThingPark does not know your AS transport key. If you lose it, you will have to generate a new one and all devices associated with this AS routing profile will have to restart a join procedure.
You must have read-write access to Device Manager For more information, see Opening a panel and checking your read-write access, an HSM installed on your operator platform and a connectivity plan with the Hardware Security Module (HSM) protection parameter set. For more information, see LoRaWAN® unicast connectivity plan details.
-
In the navigation panel, click AS routing profiles.
-> The AS routing profile panel opens.
-
In the AS routing profile frame, click the AS routing profile you want to activate the HSM, and click Edit.
-> The Hardware Security Module (HSM) frame appears in the AS routing profile if you have a connectivity plan enabled for HSM.
-
In the Hardware Security Module (HSM) frame, click Activate. If a message appears, click Yes.
-> The Generate AS transport key dialog box appears.
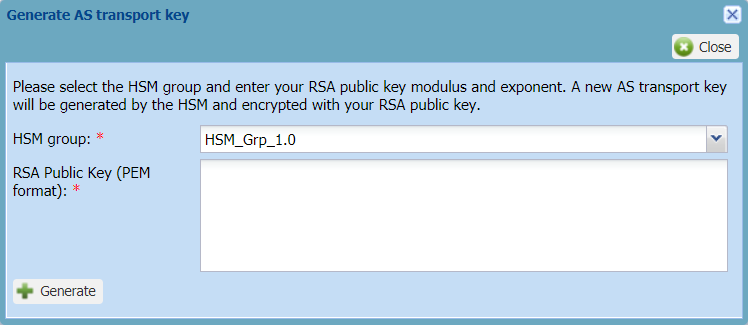
-
Using for instance an OpenSSL command in a shell terminal:
-
Generate an RSA key using the following command:
openssl genrsa -out rsa.private 1024 -
Extract the RSA public key using the following command:
openssl rsa -in rsa.private -pubout > rsa.publicHere is an example of RSA public key:
-----BEGIN PUBLIC KEY-----MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDuT5R7jWa0T4N9gwpRPNQxH62VuLYwW4qVb03DV28i0vhflIj2oERy2ahK9EawbojdY5ZOSjzeCoa8pfSgXbRNFBFdm/2xABEcI6X70iyW2g8qRZDeUA0AkGOAfqd+X52bWMgBK3TpwAVFlao6rqw3w9oWLOlVuiUsnwY/GJ2vDwIDAQAB-----END PUBLIC KEY-----
-
-
In the Generate AS transport key dialog box, copy the content of your RSA public key in the RSA Public Key (PEM format) box.
-
Click Generate.
-> The Encrypted AS transport key (hexadecimal string) box appears containing your encrypted AS transport key.
-
Click Copy.
-
Paste your encrypted AS transport key in a text file you can name for instance:
encrypted_astk.txt -
In the shell terminal:
-
Convert the encrypted AS transport key to binary using the following command:
xxd -r -p encrypted_astk.txt encrypted_astk.bin -
Decrypt the AS transport key using the RSA private key and the following command:
openssl rsautl –decrypt -inkey rsa.private -in encrypted_astk.bin -out astk.txt-> The generated astk.txt file contains your AS transport key in hexadecimal format.
-
-
Click Close.
-> Now the AS routing profile has been activated for HSM, you can associate it with an OTAA device that uses Local Joint server with HSM protection:
-
Either when creating the device.
For more information, see Creating an OTAA device. -
Or by editing it using Allocating an AS routing profile.
-> Your AS transport key in hexadecimal format is ready to be given to the owner of the application server to be configured on it.
-