Adding a basic HTTPS connection
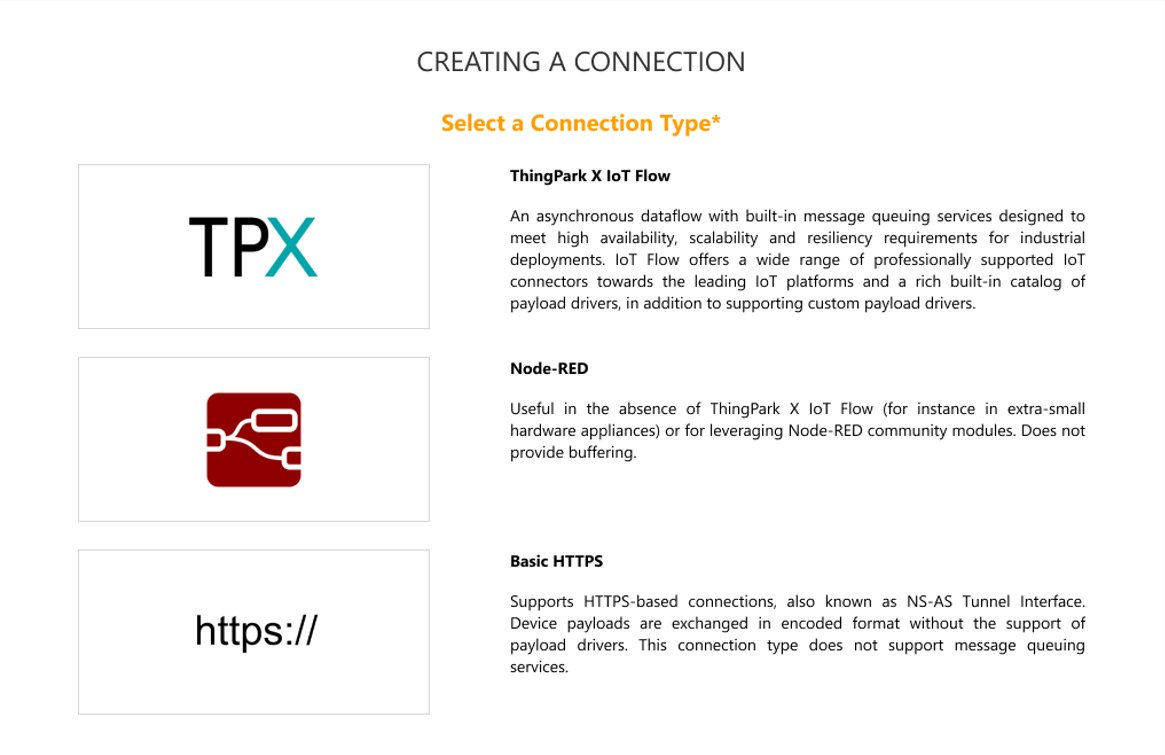
What is a basic HTTPS connection?
Basic HTTPS connections provide a direct bidirectional connection between the Network Server (NS) and third-party Application Servers (AS) using HTTPS protocol, also known as NS-AS Tunnel Interface. For security purposes, downlink messages are accepted only if an encrypted token is included in the POST. Device payloads are exchanged in encoded format without the support of payload drivers. This connection type does not support message queuing services: when the AS is temporarily unavailable or overloaded, the uplink messages will be lost. The AS may also be temporarily throttled by software fuses if it cannot keep up with uplinks.
To learn more about basic HTTPS connections and NS-AS Tunnel Interface, see ThingPark Enterprise LRC-AS Tunnel Interface Developer Guide for LoRaWAN®.
Adding a basic HTTPS connection
-
Select Connections, and click ADD CONNECTION in the Connections page, or from Dashboard, go to the CONNECTIONS widget, and click
.
-
Click the Basic HTTPS type of connection.
-
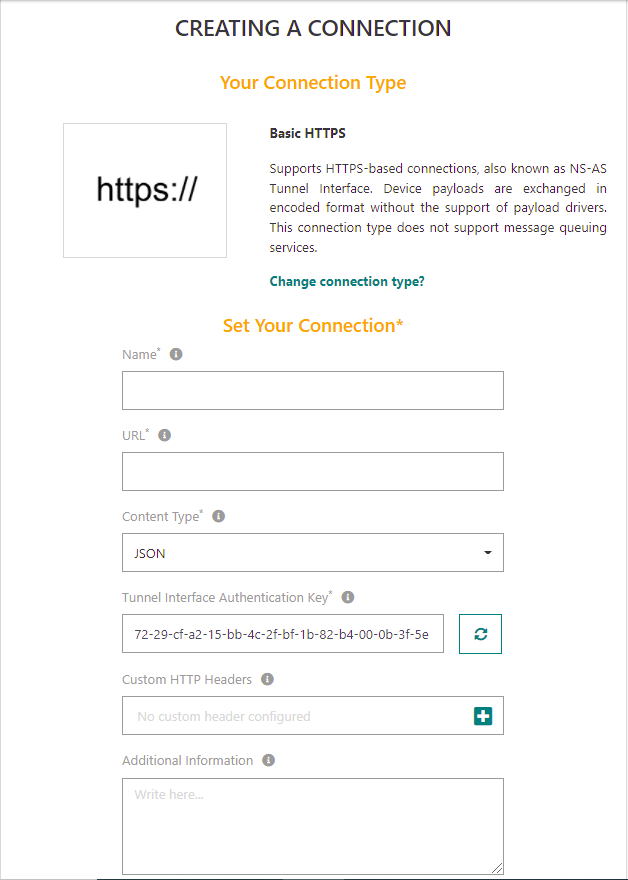
Fill in the form, aided by the following table:
Note Parameters marked with * are mandatory.
Parameter Definition Name (mandatory) Friendly name given to your connection. Domains If the permission segregation based on domains has been enabled by an administrator user, you may associate your connection with domains to restrict its visibility. See About domains for more details.
- If no domains are set, the connection is cross-domain and visible to all users.
- If your user account has domain restrictions, the associated domains must match your domain restrictions without any domain prefix (only full domains can be assigned to resources).URL (mandatory) The URL used to reach the IoT Application Server which ThingPark Enterprise shall exchange uplink and downlink messages with.
Note: The URL format must follow RFC-3986.Content Type (mandatory) The type of encoding used to report device data to your application: XML, JSON or JSON untyped format (JSON document where all values, including numeric values, are reported as strings). Tunnel Interface Authentication Key (mandatory) This system-generated security key should be shared between ThingPark and the HTTPS Application Server (AS). It is meant to provide an application-level signature to the uplink messages sent from ThingPark to AS, as well as the downlink messages sent from AS to ThingPark. This is particularly needed for downlink path, to ensure that only Application Servers having this security key can send downlink messages to your devices.
Click.
Important: You must share the regenerated key with your Application Server instead of the older one. To learn more about the use of this key, see ThingPark Enterprise LRC-AS Tunnel Interface Developer Guide for LoRaWAN®.Custom HTTP headers You may define up to 5 custom HTTP headers for each Basic HTTP connection. Each custom HTTP header is statically defined as a string (e.g., "Authorization: Bearer AbCdEf123456"). Click to Add custom headers, each header is composed of two fields:
- The Header name (see RFC 7230). Following header names are forbidden names: "Accept", "Host", "User-Agent", "Content-Length", "Content-Type", "Expect" and "Proxy-Authorization". A given header name can be configured only once (case insensitive).
- The Header value (see RFC 7230). The maximum length of an HTTP header (name + value) is 510 characters.
Specific consideration: The "Authorization" header may be explicitly defined as a custom HTTP header, but it may also be implicitly generated by the network server when the destination URL contains a login/password (e.g., http://user:pwd@application.com). When both are defined, priority is given to the login/password defined in the URL.Additional information Any useful information (for instance, administrative) that is related to the connection. -
Click ADD.