Connect Your Network Server to ThingPark Activation
As a Network Operator, the onboarding of the Network Server onto the ThingPark Activation platform is composed of three steps:
- Transport layer configuration
- Network Server and OSS configuration
- Pushing security requirements on supported Application Servers, for end-to-end encryption in particular
Transport level
Operators using ThingPark Wireless or ThingPark Enterprise SaaS platforms can skip this step.
For on-premises’ platforms, a secure transport must be established between Network Server and ThingPark Activation.
Firewall settings
NS to PROXY_HTTP (host on JS platform)
- Protocol: HTTPS, port TCP:443, TLS v1.2 (secure)
- Destination: PROXY_HTTP
- Type: unidirectional
JS to PROXY_HTTP (host on NS platform)
- Protocol: HTTPS, port TCP:443, TLS v1.2 (secure)
- Destination: PROXY_HTTP
- Type: unidirectional
PROXY_HTTP (host on NS platform) to NS
- Protocol: HTTP, port TCP:8807
- Destination: NS
- Type: unidirectional
VPN can be setup on-demand per project.
HTTPS is also supported using following parameters
- TLS1.1 or TLS1.2
- PSK
Network Server configuration
The Network Operator using ThingPark Wireless can configure the Network Server using this guide. For the Third-Party Network Server, contact your provider to configure the Network Server to behave as the following:
-
Network Server only: some Network Server include a Join Server function which should be disabled for these devices, and messages should be exchanged with an external Join Server according to LoRaWAN™ Backend Interface 1.0.
noteNS-JS interoperability tests must have been run successfully as a pre-requisite to this configuration.
-
Configure business agreements and credentials to interoperate with ThingPark Activation on homeNS, Join and ReJoin procedures
-
Configure NS-AS interface to forward encrypted AppSKey
To configure ThingPark Wireless, start by creating an offer for NS-only Device Manager. In the ThingPark Vendor account, create an offer containing the items:
- Application: Device Manager
- Application Option: external-js-opt
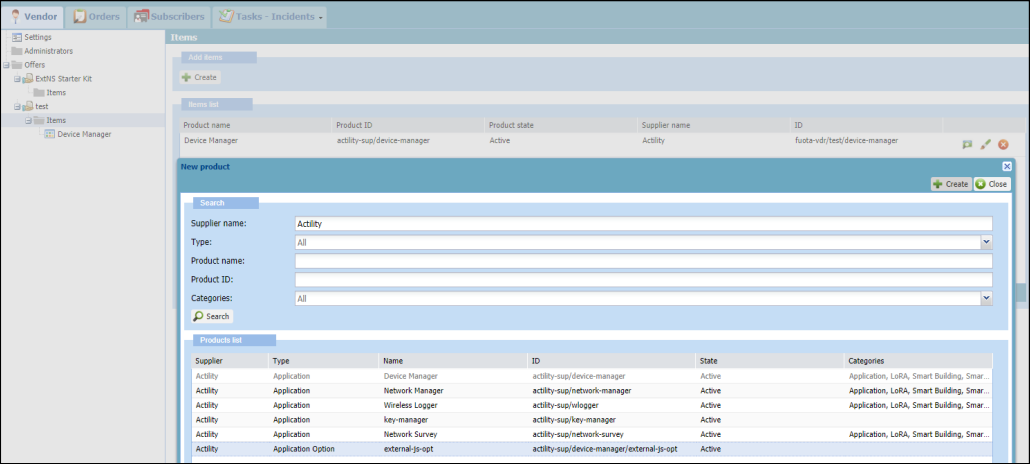
Subscribers can then order this new offer and have a Device Manager for NS-only. The Create Device’s screen should then not contain AppKey/NwkKey anymore:
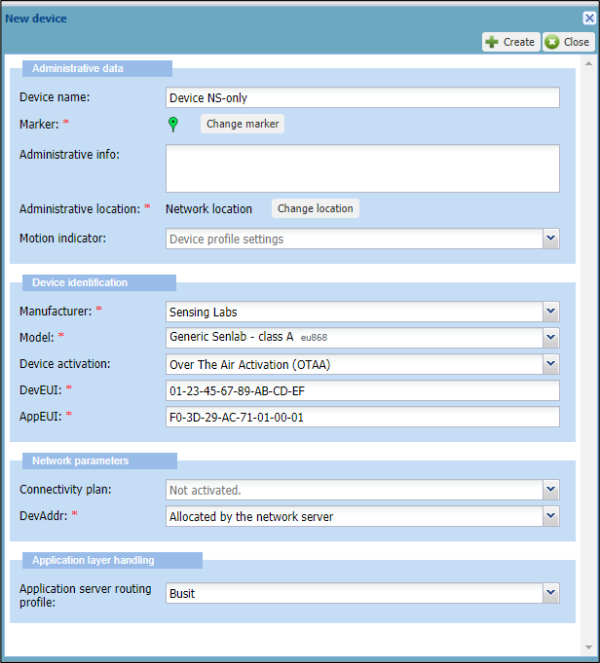
Log in as LRC-NS administrator and fill in the configuration tables as follows (AppEUI must be adapted if using a dedicated AppEUI/JoinEUI, NSID must be completed):
-
FDB_lora/TrustedOp/Net_NSID-App_f03d29ac71010001
<?xml version="1.0" encoding="UTF-8"?>
<TrustedOperator xmlns="http://uri.actility.com/lora">
<SenderID>F03D29AC71010001</SenderID>
</TrustedOperator> -
FDB_lora/FOp/Net_NSID-App_f03d29ac71010001
<?xml version="1.0" encoding="UTF-8"?>
<ForeignOperator xmlns="http://uri.actility.com/lora">
<ReceiverID>NSID</ReceiverID>
<AppEUI>F03D29AC71010001</AppEUI>
<RoutingProfileJS>js-ope1</RoutingProfileJS>
</ForeignOperator> -
FDB_lora/r/js-ope1
<?xml version="1.0" encoding="UTF-8"?>
<RoutingProfile xmlns="http://uri.actility.com/lora">
<Type>UPHTTP</Type>
<Payload>xml</Payload>
<Extend>0</Extend>
<ID>js-ope1</ID>
<Descs>
<Desc Port="\*" Type="HTTP" Strategy="ORDER">https://activation-eu.thingpark.com/thingpark/lrc/rest/js/</Desc>
</Descs>
<RoutingProfileList></RoutingProfileList>
<User>operator1</User>
<Password>password1</Password>
</RoutingProfile>
Application Server requirements
Application Servers must implement Actility HSM security requirements for end-to-end data encryption:
- ASTK provisioning/storage in the Subscriber account of the Application Server
- Support reception of encrypted AppSkey and decrypt it using AS Key
- Secure storage of the decrypted AppSKey for each subscriber
- Decryption of uplink data using AppSKey
- Encryption downlink data using AppSKey before sending to the Network Server
All details of the implementation including test vectors are available in the LRC-AS Tunnel Interface Developer Guide.