Importing devices
You may import up to 50K devices in TPE SaaS, 20K in self-hosted TPE. The CSV file must not exceed 20MB, it may include a mix of OTAA and ABP devices.
Make sure that your CSV file has the right format prior to doing the operation. A sample file is downloadable from the user interface.
-
Fom the left panel, select Devices, then click IMPORT DEVICES from the top-right corner of the page.
You can also expand IMPORT DEVICES and select Import from CSV file. -
Prepare your .csv import file, guided by the SAMPLE FILE downloadable from the user interface. To learn more about how to build your .csv file, see Devices import file.
noteYou will need to fill the Device Model ID for each imported device. Use the downloadable MODELS LIST file to get the mapping between each model and its ThingPark Model ID.
Only device models compatible with the list of enabled ISM bands are returned. -
Optional: In case you do not want to import the keys of your devices in clear-text format, you may import RSA-encrypted keys by applying the following steps, leveraging asymmetric cryptography:
-
In the user interface, click the public key to download the RSA public key that you should use to encrypt the keys of your devices. The downloaded file includes the public key in JWK (JSON Web Key) format.
-
Convert the
JWKformat toPEMformat. Let's denote the resulting keypubkey.pem.tipTo do this conversion, you may use an online converter such as https://8gwifi.org/jwkconvertfunctions.jsp
-
Using
pubkey.pem, encrypt your device keys, for instance using OpenSSL, then convert them to base64 format.tipAs an example, to encrypt a hexadecimal AppKey, you may use the following OpenSSL commands in a shell terminal:
xxd -r -p AppKey.hex > AppKey.bin
openssl pkeyutl -encrypt -in AppKey.bin -out encryptedAppKey.bin -pubin -inkey pubkey.pem -pkeyopt rsa_padding_mode:pkcs1
base64 encryptedAppKey.bin > encryptedAppKey.b64 -
Add your encrypted keys, in base64 format, to your CSV file and fill column X of this CSV file with the key ID provided by the
kidfield of the JWK file downloaded in step-1 above.
-
-
When your CSV file is ready, click
to upload it.
-
If the permission segregation based on domains has been enabled by an administrator, associate your device with Domains. If your user account has domain restrictions, the associated domains must match your domain restrictions without any domain prefix (only full domains can be assigned to resources). See About domains for more details.
-
Click IMPORT.
-> The mass import processes. Colored toasters display on your screen to inform you about its progress. The screen to inform you about its progress. The progression follows this sequence:
-
The request is pending (dark green).
-
Then, the import completes with one of the following states:
-
The task is completed and the device import has failed (orange).
-
The task is completed and the device import has failed (orange).
-
The task is completed and the device import is successfully done
-
The task is completed and the device import is successfully done (green).
-> When the mass import is complete, a notification displays in the Top Bar indicating the results of the import. It can be one of the following:
-
The device import is successfully done.
-
The device import has succeeded with errors.
-
The device import has failed.
-
-
-
-
From the top-right corner of the user interface, click
to access the Notifications list. To learn more, click About device notifications.
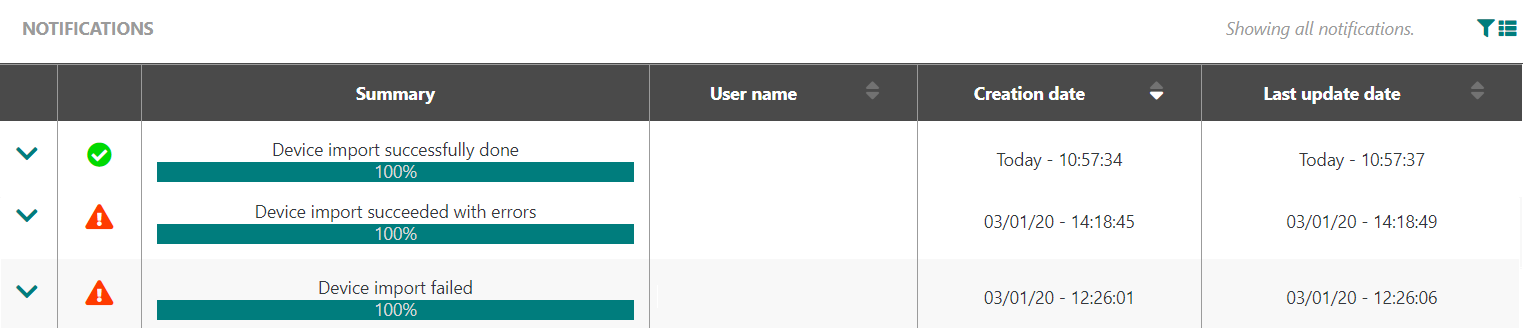
- If the mass import has not succeeded, analyze and correct errors in the .CSV file then re-import the file.
A device addition matching a DevEUI already existing and belonging to the same subscriber triggers an error and is counted in the “Error” counter. The import process is aborted when there are 100 errors.
- After a successful mass device import, go to the devices' list to view all imported devices.