Activation modes
Depending on the level of security that you want to allocate to your IoT network , you can choose among three types of device activation. The security relies on the keys that are associated with your device. The activation modes are listed below from most secure to less secure:
-
Over-the-Air Activation (OTAA) with external Join Server: The root keys included in the device are pre-commissioned by the manufacturer in an external Join Server. The Join procedure generate session keys that are renewed during each Join. This process make the OTAA with external Join Server the most secured activation mode.
-
Over-the-Air Activation (OTAA) with local Join Server: The root keys included in the device are not pre-commissioned by the manufacturer in an external Join Server but directly provided to the device owner. This activation is less secure than OTAA with an external Join Server since the root keys can be exposed to third-parties or be lost by the device owner.
-
Activation By Personalization: The device does not include root keys and only includes session keys that are not renewed during each Join, since there is no Join procedure with Activation by Personalization.
The figure below shows the OTAA with ThingPark Activation (TPA) as an external Join Server:
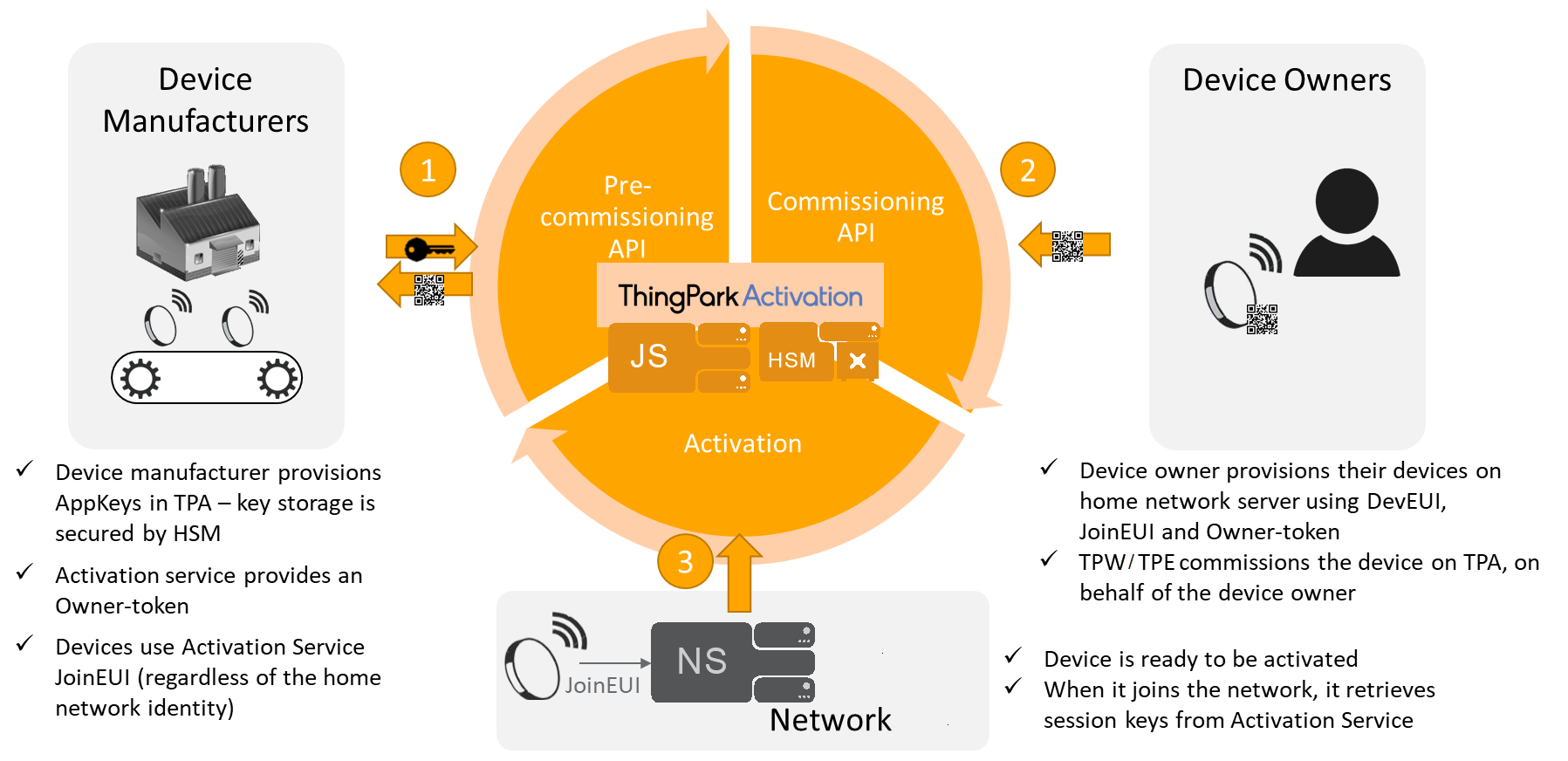
Over-the-Air Activation is the most secure way to connect with devices into the network. Devices perform a Join-procedure with the network, during which a dynamic DevAddr is assigned and security keys (NWKskey and AppSKey) are negotiated with the device. To learn more about keys, click Devices' parameters.
Using a secure activation service significantly secures the exchange process between device manufacturers and device owners. The root keys are securely provisioned by the device manufacturer in the Join Server and do not need to be directly shared with the device owner. Only the owner token is communicated to the device, as a proof of ownership during claim process.
For more information, see Integration with ThingPark Activation (TPA) service (RDTP-3381).
Note Session keys (NwkSKey et AppSKey) for ABP devices are not renewed regularly as opposed to OTAA devices' session keys.
Characteristics of the OTAA activation modes
| Local Join Server - Activation mode does not include pre-commissioning | External Join Server - Activation mode includes pre-commissioning |
|---|---|
The Activation Service (LoRaWAN®Join Server) is embedded in your ThingPark platform. You enter the Appkey that your manufacturer has provided you with in your ThingPark platform. Since the AppKey is communicated to you, this activation mode is less secure. | The Activation Service uses a separate/external Join Server located outside of your ThingPark platform. Your manufacturer enters the Appkey in your external Join Server for you. If the external Join Server is ThingPark Activation, you can enter an owner token to automate the claim of the device's ownership in ThingPark Activation. Otherwise, the claim procedure must be performed out of band. Since the AppKey is not communicated, this activation mode is more secure. |
OTAA and ABP activation modes
| Type of activation | Type of commissioning | Format | Type of tasks | Task |
|---|---|---|---|---|
| OTAA | Manual provisioning with a local Join Server (level of security 1) | Creation form | Repeat the task for each of your devices | Manual provisioning of OTAA and ABP devices |
| OTAA | Manual provisioning with an external Join Server (level of security 2) | Creation form | Repeat the task for each of your devices | Manual provisioning of OTAA and ABP devices |
| OTAA | Simplified provisioning | External Join Server | QR code | Repeat the task for each of your devices |
| OTAA | Mass import | Local/External Join Server | CSV file | Do the task once for each of your imports |
| ABP | Manual provisioning | Creation form | Repeat the task for each of your devices | Manual provisioning of OTAA and ABP devices |
| ABP | Mass import | CSV file | Do the task once for each of your imports | Importing devices in 2 steps |
Note For already-provisioned devices, the activation mode is displayed in the device detail page from ThingPark user interface. To learn more, see Updating device parameters, and viewing/editing device details