Cisco IXM
ThingPark supports the Cisco IXM standalone model (also known as Corsica).
The multi-box model (also known as warbler) is end-of-life and no longer supported by the latest LRR versions.
Software pre-requisites and compatibility matrix
| Base Station Model | LRR Version | Firmware Version | FPGA Version |
|---|---|---|---|
| Cisco IXM | 2.8.54 | 2.3.2 | 61 |
If your base station's FPGA version is not at the version stated, you need to first upgrade the base station with an OS image that has the desired FPGA version. For further details, refer to the Cisco documentation.
To upgrade your base station's firmware version, see the procedure provided in Installing Cisco IXM Firmware.
LRR installation
After downloading the base station image as described in Retrieving the base station image, follow the steps provided below to flash your base station with the new image.
Host console access
The first steps of the installation process require access on the host console. Follow the below diagram to connect to the terminal:
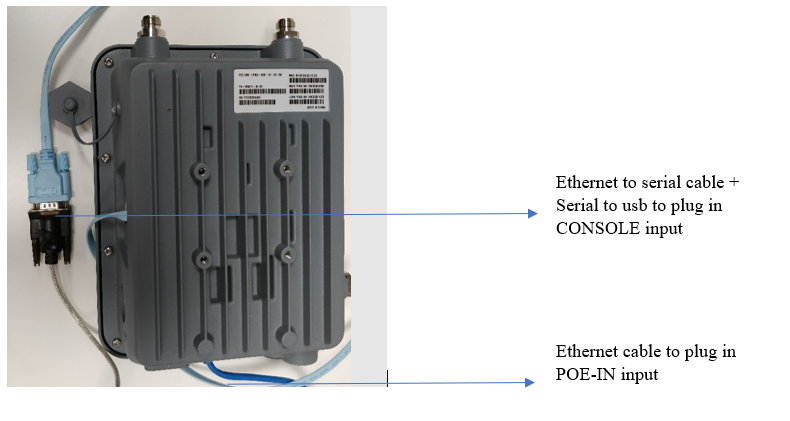
Then, use the terminal emulator with the following configurations:
| Baud rate | 115200 |
| Data | 8-bit |
| Parity | None |
| Stop | 1 bit |
| Flow Control | none |
Note If you are not familiar with Cisco IXM LoRaWAN® CLI interface, you may refer to Cisco IXM LoRaWAN® documentation:
First, you must enable the CLI console:
enable
# It should go from
# Gateway>
# to
# Gateway#
If your base station comes with factory settings: no password is required to access the console.
If your base station already has a LRR Software installed: You need to provide the password (secret) that you have set during the first installation.
Checking the firmware version
To get and verify versions, run the "show inventory" command:
show inventory
# Name : Gateway
# ImageVer : 2.3.2
# BootloaderVer : 20180130_cisco
# SerialNumber : FOC20304ZDA
# PID : IXM-LPWA-800-16-K9
# UTCTime : 12:01:17.844 UTC Fri Jun 21 2024
# FPGAVersion : 61
# FPGAStatus : Ready
# ChipID : LSB = 0x28750a03 MSB = 0x00f14086
# TimeZone : UTC
# LocalTime : Fri Jun 21 12:01:17 UTC 2024
# ACT2 Authentication: PASS
Your acquired Cisco base station should come with those FPGA and Cisco IXM Firmware versions. If not, contact your Cisco partner, distributor or reseller and refer to Cisco IXM documentation. To learn more about IXM LoRaWAN® firmware update and release notes, see the Cisco documentation.
Preparing the USB install key or TFTP server
Extract the LRR Software package <LRR_SOFTWARE_PACKAGE_FILENAME>
(.tar.gz file) previously downloaded with the following command:
tar -zxvf <LRR_SOFTWARE_PACKAGE_FILENAME> -C <DESTINATION PATH FOLDER>
The software package contains the following files:
-
<lrr installation package>: the LRR installation package (.cpkg file) -
<ixm firmware>: the firmware package to be installed (.tar.gz file) -
<pubkey file>: the pubkey needed to allow the LRR installation (.pubkey file).
All files above need to be copied into a USB stick file system or on a TFTP server depending on the method you will use to flash the base station.
Installing Cisco IXM Firmware
Only if your IXM LoRaWAN® gateway is not running release 2.3.2, you need to install the Cisco IXM base station firmware.
If you are using TFTP to transfer the IXM firmware file on base station, run the following command:
copy tftp://<tftp server address>/<ixm firmware> flash:
If you are using usb to transfer the IXM firmware file on base station, run the following command:
usb enable
copy usb:/<ixm firmware>flash:
Install the Cisco IXM base station firmware with the below archive command on CLI (host console):
archive download-sw firmware /factory /save-reload flash:<ixm firmware>
Note <ixm firmware> should be changed to match the version and
software itself.
Note /factory option is recommended to avoid potential problems
while performing upgrade.
Transferring installation packages
If you are using TFTP to transfer the installation packages on base station, run the following command:
copy tftp://<tftp server address>/<lrr installation package> flash:
copy tftp://<tftp server address>/<pubkey file> flash:
To display the files under flash directory, run the following command:
dir flash:
Note Cisco IXM base station is delivered with its firmware pre-installed in manufacturing, therefore it should not be necessary to copy and install the IXM firmware file.
If you are using USB to transfer the installation packages on the base station, run the following command:
usb enable
copy usb:/<lrr installation package> flash:
copy usb:/<pubkey file> flash:
Running configuration settings for host machine
Note All the settings done in this section are on the host machine. The LRR software requires an account created on the host machine for CLI access through a "ssh" connection. Perform the configuration with the commands provided below:
- Enable the CLI configure terminal to set the following configurations:
configure terminal
- Username and password creation (this username and password are the ones used to connect via ssh):
# in Gateway(config)# mode
username actility password actility
- Secret enablement (this password is the one used to enable host console):
# in Gateway(config)# mode
enable secret cisco
- SSH enablement:
# in Gateway(config)# mode
crypto key generate rsa
- SSH from outside gateway enablement:
# in Gateway(config)# mode
ip ssh admin-access
-
IP/DHCP settings
- IP domain lockup:
# in Gateway(config)# mode
ip domain lookup
- IP name server:
# in Gateway(config)# mode
ip name-server 8.8.8.8
ip name-server 8.8.4.4
- Interface(VLAN/DHCP) setting:
# in Gateway(config)# mode
interface FastEthernet 0/1
# in Gateway(config-if)# mode
ip address dhcp
# or
ip address <IP_address> <Netmask>
Note The example above describes how to set-up an IP address on the FastEthernet 0/1 interface. If a VLAN interface should be configured, see Cisco documentation to set it up.
Note If you have enabled DHCP, you can retrieve the IP address of the base station with the following command:
show ip interface FastEthernet 0/1
- Radio status:
show radio
# LORA_SN: FOC21028R30
# LORA_PN: 95.1602T01
# LORA_SKU: 915
# LORA_CALC: <NA,NA,NA,54,35,110,101,92,84,75,67,57,48,39,30,21-NA,NA,NA,53,35,108,99,91,82,74,66,57,48,39,30,21>
# CAL_TEMP_CELSIUS: 33
# CAL_TEMP_CODE_AD9361: 89
# RSSI_OFFSET: -204.00,-205.00
# LORA_REVISION_NUM: C0
# RSSI_OFFSET_AUS: -203.00,-203.00
# radio status:
# on
Note If radio status not on, enable with following command:
# in Gateway(config)# mode
no radio off
- Saving startup configuration:
# in Gateway(config-if)# mode
exit
# in Gateway(config)# mode
exit
copy running-config startup-config
Note You may check the running-config with the following command:
show running-config
Installing packet forwarder (LRR)
The packet forwarder installation corresponds to the LRR software and custom configurations setup.
- Ensure the LRR package and pubkey exist in the flash drive:
dir flash:
- Check if there is existing LRR software installed and uninstall it if exist.
show packet-forwarder info
If there is existing LRR software up and running, stop the service and uninstall it before proceed to next step. If not, skip the following steps:
configure terminal
# in Gateway(config)# mode
packet-forwarder stop
packet-forwarder uninstall firmware
exit
- Install the public key you have extracted during the step " Preparing the USB install key or TFTP server":
configure terminal
# in Gateway(config)# mode
packet-forwarder install pubkey flash:<pubkey file>
- Once the pubkey file is installed, install the LRR using the following command and reload the gateway to properly start the necessary services :
# in Gateway(config)# mode
packet-forwarder install firmware flash:<lrr installation package>
packet-forwarder start
exit
reload
-
Once the packet forwarder is installed and the gateway has reloaded, wait for 5 minutes to allow the LRR background tasks to complete the setup of the CLI setting.
-
After 5 minutes, check the packet forwarder status and check the running-configuration and NTP server list, the settings shall be as shown below:
show packet-forwarder status
# Status : Running
show packet-forwarder status
# Status : Running
show running-config
# Warning: Try to get lock. Please wait...
# !
# enable secret 8 ****
# !
# hostname Gateway
# !
# interface FastEthernet 0/1
# ip address dhcp
# exit
# !
# username actility password 8 ****
# !
# radio off
# ip ssh admin-access
# !
# ntp server ip 0.pool.ntp.org
# ntp server ip 1.pool.ntp.org
# ntp server ip 2.pool.ntp.org
Finally, you must exit the configuration mode first and then enable the container console
# in Gateway(config)# mode
exit
request shell container-console
# Password: admin
You may then access SUPLOG to verify that the LRR version installed on the base station is as per the version stated on the ThingPark base station image.
For Cisco IXM base station, the LRR is installed in a container. To access the SUPLOG menu, connect in SSH to the base station using the IP address, the username and the password set during the step "Running configuration settings for host machine".
Once you have enabled the CLI console, you need to request access to the LXC and connect to support account.
The password asked while enabling host command line is the secret you had set during configuration:
enable
# Password (secret)
request shell container-console
# Password: admin
# bash-3.2
su support
You also need to edit the credentials.txt file in the LRR within the container:
enable
# Password (secret)
request shell container-console
# Password: admin
# bash-3.2
vi /tmp/mdm/pktfwd/firmware/usr/etc/lrr/credentials.txt
The credentials.txt file holds the following information (in this order):
IXM "secret" password IXM username IXM user's associated password.
Please edit the file with the 3 passwords you configured.
Note Especially for SAAS installation, this is required for the base station to automatically download its IPSEC certificates and allow remote operations and troubleshooting. A reboot of the base station after the file is updated is needed to complete the connection towards the ThingPark SaaS core network.
You may also verify the base station with the following command:
cat $ROOTACT/usr/etc/lrr/versions.ini
Upgrade Cisco IXM without factory reset and LRR upgrade
1. Cisco IXM firmware upgrade from v2.2.0 to v2.3.2 or from v2.3.1 to v2.3.2
For the Cisco IXM firmware upgrade without factory reset, you may use image installation with /normal option instead of /factory option. The Cisco image installation command should be as below, assuming the Cisco image has already been placed under the flash: directory:
archive download-sw firmware /normal /save-reload flash:ixm_mdm_i_k9-2.3.2.tar.gz
After the firmware has been installed, the gateway will automatically reload.
Once the gateway boots up, it should appear as connected in the ThingPark GUI within 15 minutes. If it does, you may proceed with Step 2: LRR software package upgrade.
However, for gateways that require a certificate to establish an IPSec or TLS tunnel, a failure to connect within 15 minutes may indicate a known issue (ref: PT-2535), where the certificate may be missing on the host after a firmware reload. This can result in failed connection attempts. In such cases, please follow the steps below to restore connectivity:
Step 1: Clean up old certificates
- Request access to the container console:
request shell container-console
- From the SUPLOG root menu (su - support), navigate to:
System Configuration → PKI → Cleanup Certificates
- Apply and Commit the operation
Step 2: Regenerate certificates and reload
-
Reload the gateway to restart both the host system and the LRR container.
-
While the gateway is restarting, log into your account on the ThingPark portal.
-
Navigate to the Base Station details page, go to the Advanced tab, and under the Security widget, click Regenerate.
This step regenerates the security certificate for the base station, which is required to correctly re-establish a secure backhaul link between the gateway and the ThingPark Core Network.
By using /normal option in flashing the Cisco image, the gateway shall be able to reconnect to the Network Server after gateway reboot. Note that after the gateway boots up, radio may not work accordingly due to incompatible Cisco firmware and LRR software version. This issue shall be lifted once the new LRR software package has been installed on the gateway.
2. LRR software package upgrade to LRR version 2.8.54 via ThingPark GUI from either version 2.6.53 or 2.8.36
After upgrading the gateway to Cisco firmware version 2.3.2, follow these steps to upgrade the LRR software:
For TPE OCP platform users with Cisco IXM gateway running LRR versions earlier than 2.8.54, you may encounter the known issue PT-2719, where LRR upgrades fail due to the absence of the lrr-opk.pubkey on the platform. As a prerequisite, run the following command to check if the lrr-opk.pubkey is present. If it is missing, please contact support for assistance. If the file is present, you may proceed with the LRR upgrade.
docker exec -it $(docker ps -q -f "name=actility_ftp") /bin/sh -c "ls -lrt /var/ftp/ftp-lrc/lrr-opk.pubkey"
-
Log in to your account on the ThingPark portal and navigate to the detailed page of the base station.
-
In the Basic View tab, locate the Information widget and click the Upgrade button next to the Packet Forwarder field.
-
Once the upgrade is complete, go to the Advanced tab and find the Security widget.
-
Click the Regenerate button to regenerate the security certificate for your base station. This step is necessary to establish a secure backhaul link when connecting to the ThingPark core network (whether IPSec-based or TLS-based).
Due to a known limitation (PT-2513), the GUI may display the error message: "The base station upgrade has failed because the upgrade command returned an error." during the upgrade process. This error message can be safely ignored.
Once the LRR upgrade is complete, the gateway will automatically reload. After rebooting, it will reconnect to the network server and download its new certificate.
The GUI should update to reflect the new LRR version once the upgrade is successfully installed.
This process may take approximately 20 minutes to complete.