Managing the base station's security
About base station's security
For Saas deployments, base stations must connect to ThingPark's core network through a secure backhaul, either using IPSec or TLS protocol. TLS is the recommended security protocol as it is easier to establish, more NAT-friendly and offers the best authentication and encryption flows.
For self-hosted deployments, while the use of a secure backhaul connection between base stations and ThingPark's core network is still recommended, it is up to the platform administrator to enforce it in their network.
To use a secure connection, each base station must download an X.509 certificate from ThingPark's Public Key Infrastructure (PKI), more precisely the Key Installer server. This certificate-based authentication allows certifying that the base station is indeed the one it claims to be. Thus, only authenticated base stations are authorized to connect to the platform.
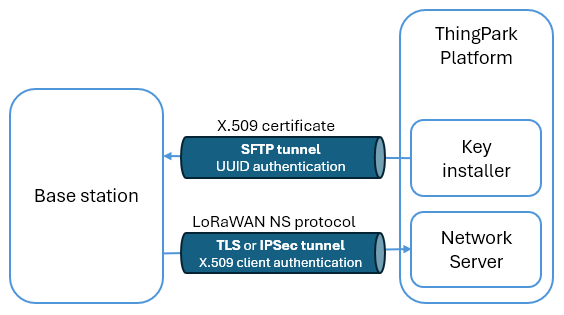
For the utmost security, BS access to ThingPark SaaS Key Installer is authenticated by public-key cryptography, also known as asymmetric cryptography. In this mechanism, each base station using the LRR packet forwarder is associated with a pair of public and private keys that are randomly generated by the LRR:
- The private key never goes outside the LRR and cannot be disclosed to the base station manager.
- The public key can be exposed externally and must be known to ThingPark's core network to allow the BS to access the Key Installer and download its X.509 certificate. To learn more about managing the public key, see Viewing/modifying the public key.
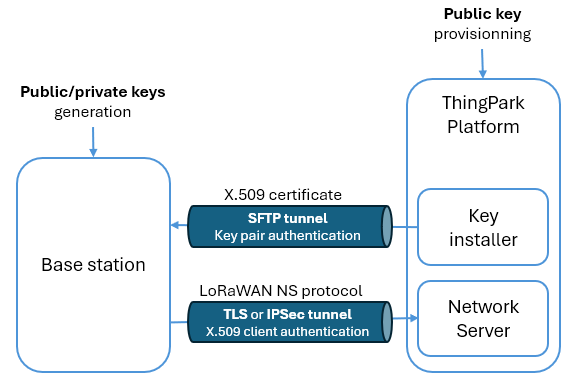
For self-hosted deployment, the BS access to the Key Installer is not authenticated by public/private key pair. It uses password-based authentication.
Once the BS successfully authenticates with the Key Installer, it can download its X.509 certificate, and then establish the secure TLS connection (or the IPSec tunnel). The default validity of the BS certificate is 2 years. When the current BS certificate is about to expire, the BS autonomously connects to the Key Installer to download its new certificate few days (6 by default) before expiration.
Viewing/modifying the public key
Viewing the current public key may be useful to troubleshoot BS connection issues, by comparing the public key declared on ThingPark with the one currently set in the LRR to ensure they are the same.
You may also execute this task to modify the public key on ThingPark's core network after generating a new public/private key pair in the LRR as per Generating and retrieving the base station's public key, for instance after a factory reset of the base station or to mitigate a security issue.
The public key declared on ThingPark must be the same as the public key locally set in the LRR. To manage the public key on LRR side, connect to SUPLOG and follow the steps described in Generating and retrieving the base station's public key
If a public key has been already declared for your base station, run the following steps to view or modify it:
-
Select the base station you want to edit. You may search it by its name or ID.
-
In the Advanced tab, under the SECURITY widget, click the MANAGE button beside the Public key.
-
To set a new public key, paste the full text including the BEGIN PUBLIC KEY and END PUBLIC KEY lines.
noteMake sure you do not have trailing spaces at the end of each line, you may use Notepad to verify this.
When you are done, click SAVE.
Regenerating the BS certificate
You may regenerate the X.509 certificate of your base station, this action automatically revokes the previous certificate.
You may use this task in the following situations:
- If the current certificate has been compromised, so you must revoke it and regenerate a new certificate.
- If you want to change the backhaul security mode of your BS from IPSec to TLS.
- If your BS has lost its current certificate for any reason, for instance, it has been cleaned up by mistake in SUPLOG.
When the current BS certificate is about to expire, a new certificate is automatically regenerated by the system and downloaded by the BS. Hence, there is no need to manually generate a new BS certificate from the user interface in this case.
The recommended procedure to apply if the X.509 certificate of the BS has been compromised is:
- From the LRR SUPLOG: the public/private key pair must be regenerated as described in Generating and retrieving the base station's public key.
- From ThingPark's user interface, update the public key to use the newly generated one, as described in viewing/modifying the public key.
- From ThingPark's user interface, regenerate the X.509 certificate as described hereunder. This action will automatically invalidate/revoke the previous (compromised) certificate.
If the access to your BS has been compromised (for instance, it was stolen), do not regenerate its certificate. The BS must be deleted from ThingPark, as described in Deleting a BS.
To regenerate the BS certificate:
-
Select the base station you want to edit. You may search it by its name or ID.
-
In the Advanced tab, under the SECURITY widget, click the REGENERATE button beside the Base station certificate.
tipTo know the expiration date of the current certificate, hover your pointer on the text displayed in grey beside the field "Base station certificate".
-
In the following dialog box, click Confirm. -> The new certificate will be immediately generated by the system and downloaded by the base station within the following 15 minutes.
Switching the BS from IPSec to TLS security mode
TLS is the recommended backhaul security mode. If your base station currently uses IPSec, you may switch to TLS by applying the following procedure:
-
If the current LRR version is 2.6.x:
-
The LRR must be first upgraded to the latest version 2.8.x. To learn more, see Upgrading the LRR.
-
Establish remote access to the base station, from the Advanced tab > REMOTE ACCESS widget > OPEN SESSION button.
-
Once you are connected to SUPLOG, go to System configuration > PKI > Cleanup certificates, then click Confirm.
-
Exit the remote session and go back to ThingPark's user interface, then regenerate the BS certificate from the Advanced tab > SECURITY widget.
-
Open a new remote SUPLOG session and switch from IPSec to TLS, as described in Activating a secure connection via IPSec or TLS.
-
Once the LRR connection is stable, trigger a backup as described in Performing backup and restore.
-
-
If the current LRR version is 2.8.x and the BS certificate was already renewed after the installation/update to 2.8):
-
Establish remote access to the base station, from the Advanced tab > REMOTE ACCESS widget > OPEN SESSION button.
-
Switch from IPSec to TLS, as described in Activating a secure connection via IPSec or TLS.
-
Once the LRR connection is stable, trigger a backup as described in Performing backup and restore.
-
Changing the password of the support account
It is strongly recommended to change the default password of the support account. This command is only supported by base stations using the ThingPark LRR packet forwarder.
This feature is supported from LRR version 2.8.39 onwards.
-
Select the base station you want to edit. You may search it by its name or ID.
-
Go to the Advanced tab > REMOTE ACCESS widget. Then on Support account's password line, click the CHANGE button.
-
A new window opens to enter twice the new support account's password.
cautionOnly strong passwords are allowed.
-
Click SAVE to change the password, otherwise click CANCEL to abort.
The new password is automatically stored by ThingPark so that the user is not requested to enter it again every time a new remote session is initiated.
When restoring a backup of the LRR software and configuration, the support password in use at the time of the backup is restored. In this case, the password stored in ThingPark may be no longer valid and must be manually entered by the user when opening a remote session from the user interface.